Modern endpoint protection for every environment
Protect Microsoft 365 and Google Workspace with multi-layer filtering, post-delivery remediation, and automated response.
Modern endpoint protection for every environment
Prevent, detect, and respond across Windows, macOS, and Linux—correlated with identity, email, and network signals.
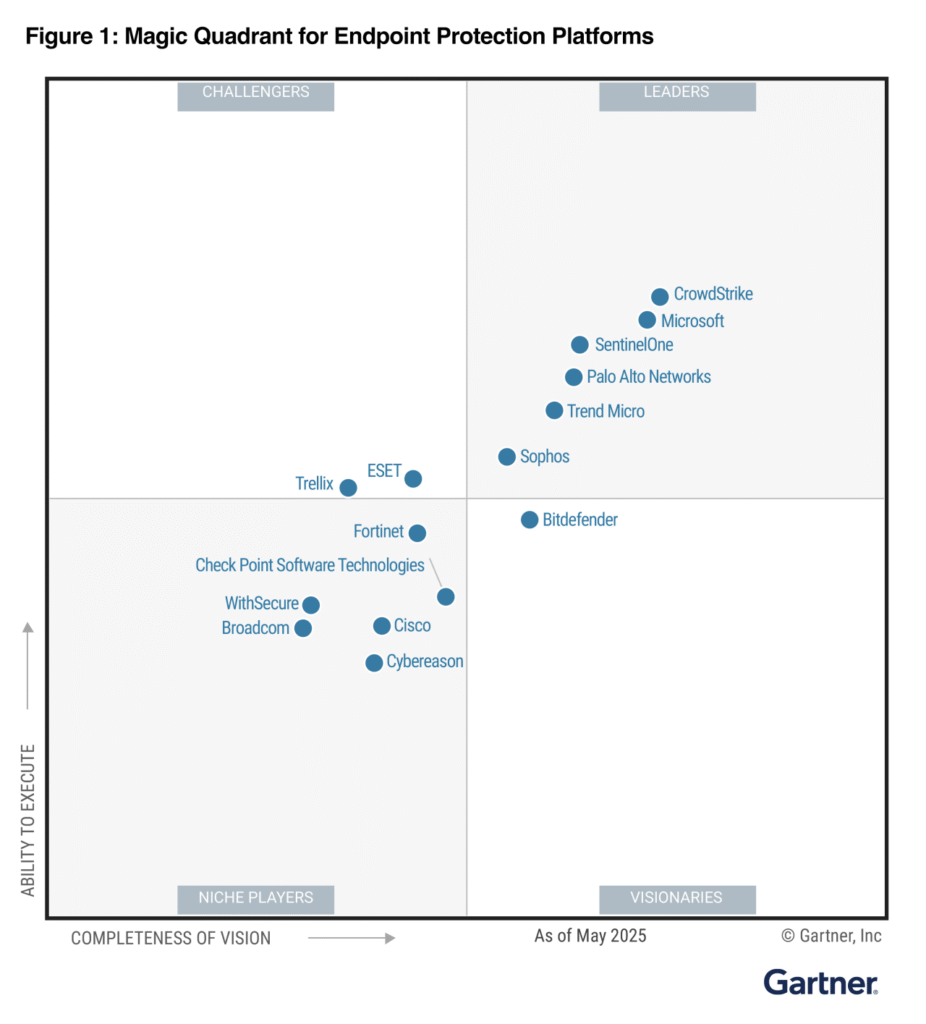
Vendor Product Technologies
With flexibility to only use what you need, when you need it – combine one or more of our products for a tailored solution.
Falcon Platform
- IOA-based prevention with Threat Graph analytics
- OverWatch MDR for 24×7 hunting & triage
- Ransomware rollback and rapid host isolation
- CrowdStrike Store integrations & open APIs

Defender for Endpoint / Defender XDR
- Advanced Hunting (KQL) across endpoint & M365 signals
- Attack Surface Reduction & vulnerability management (TVM)
- Unified Defender XDR incidents (email/identity/cloud)
- Native Intune/Entra & M365 ecosystem integration
Cortex XDR
- Behavioral analytics with BIOCs & rich endpoint telemetry
- Cortex Data Lake correlation with PAN NGFW/SASE
- XQL search for investigations & hunting at scale
- Tight playbooks with Cortex XSOAR
Singularity XDR
- Storyline™/ActiveEDR automatic attack storyline
- 1-click remediation with ransomware rollback
- Scripted, autonomous response across endpoints
- Broad ecosystem via Singularity Marketplace

Broadcom (Symantec)
- Insight/SONAR reputation & behavior analytics
- Cloud console (ICDm) with EDR investigations
- Granular device/app control & lockdown
- Email/Secure Web Gateway & DLP ecosystem

Sophos
- Deep Learning malware detection + exploit prevention
- CryptoGuard rollback for ransomware recovery
- Sophos MDR with case summaries & guidance
- Synchronized Security with Firewall/Email/Cloud
-65%
-48%
99.99%
>250k
OUR SERVICES
What We Offer You
We help create succsessfull digital products, for any screen and for ever imagenably user
Endpoint Protection & XDR
Next-gen AV and EDR with cross-domain XDR that correlates identity, email, and network signals.
Ransomware Readiness & Recovery
Hardening policies, rapid host isolation, and file/process rollback to minimize impact and downtime.
Backup
Capabilities deep-dive
Explore what each capability delivers, why it matters, and how we measure success.
Continuous, high-fidelity endpoint signals with fast query and proactive hunting.
What it is: Collect process, file, network and registry events from every endpoint—live and historical.
Why it matters: Builds a full attack timeline to reduce blind spots and accelerate root-cause analysis.
Do with it: Pivot by user, host, hash, domain; run saved queries; auto-enrich with MITRE ATT&CK.
Outcomes/KPIs: Lower MTTD and MTTR, higher investigation throughput, fewer false positives.
One-click isolation to stop spread while investigations proceed safely.
What it is: Quarantine a device at the network level; allow only console/IR traffic if needed.
Controls: Block inbound/outbound, kill malicious processes, freeze persistence changes, optional USB lock.
Workflow: Isolate → verify remediation → auto/un-isolate with approval and notes.
Outcomes/KPIs: Contain ransomware lateral movement; time-to-isolation under minutes; fewer re-infections.
24×7 threat hunting and incident response from certified analysts.
Coverage: Always-on monitoring, enriched detections, threat intel, and adversary pursuit.
Services: Triage, containment guidance, case management, executive summaries, and post-incident reports.
Engagement: Clear SLAs, named contacts, and hand-off to your SOC or our IR team when needed.
Outcomes/KPIs: Faster containment, reduced alert fatigue, audited response steps, measurable risk reduction.
Build automations and integrations across SIEM, SOAR, ITSM, cloud, and identity.
APIs: REST/Graph endpoints for detections, devices, investigations, actions, and custom intel.
Integrations: Native connectors for M365/Entra, ServiceNow, Splunk, QRadar, Cortex, and more.
Automation: Webhooks + playbooks for enrich → contain → notify → ticket, end-to-end.
Outcomes/KPIs: Shorter response loops, higher SOC efficiency, platform TCO savings.
Explore related solutions
Secure, elastic desktops and apps—built for hybrid work and zero-drama operations.
Fast, secure VDI/DaaS with stable profiles, optimized calls, and day-2 automation.